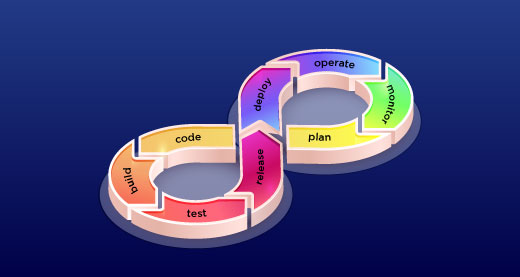
Six Principles to defend an organization against Cyber Threats
Managing cyber risk across a modern enterprise is immensely difficult. Securing complex architectures and ensuring compliance is a constant challenge, with the protection of sensitive data like PII, ePHI, and intellectual property always on the line. The solution lies in integrating your security capabilities to provide consistent visibility and protection—whether data lives on traditional systems,… Read More »